Select Language:
Ultimate Guide to Essential Cybersecurity Tools
In today’s digital landscape, robust cybersecurity measures are paramount for individuals and organizations alike. With cyber threats evolving constantly, having the right set of tools for various cybersecurity tasks can make all the difference. Here’s a detailed overview of essential cybersecurity tools categorized for easier navigation.
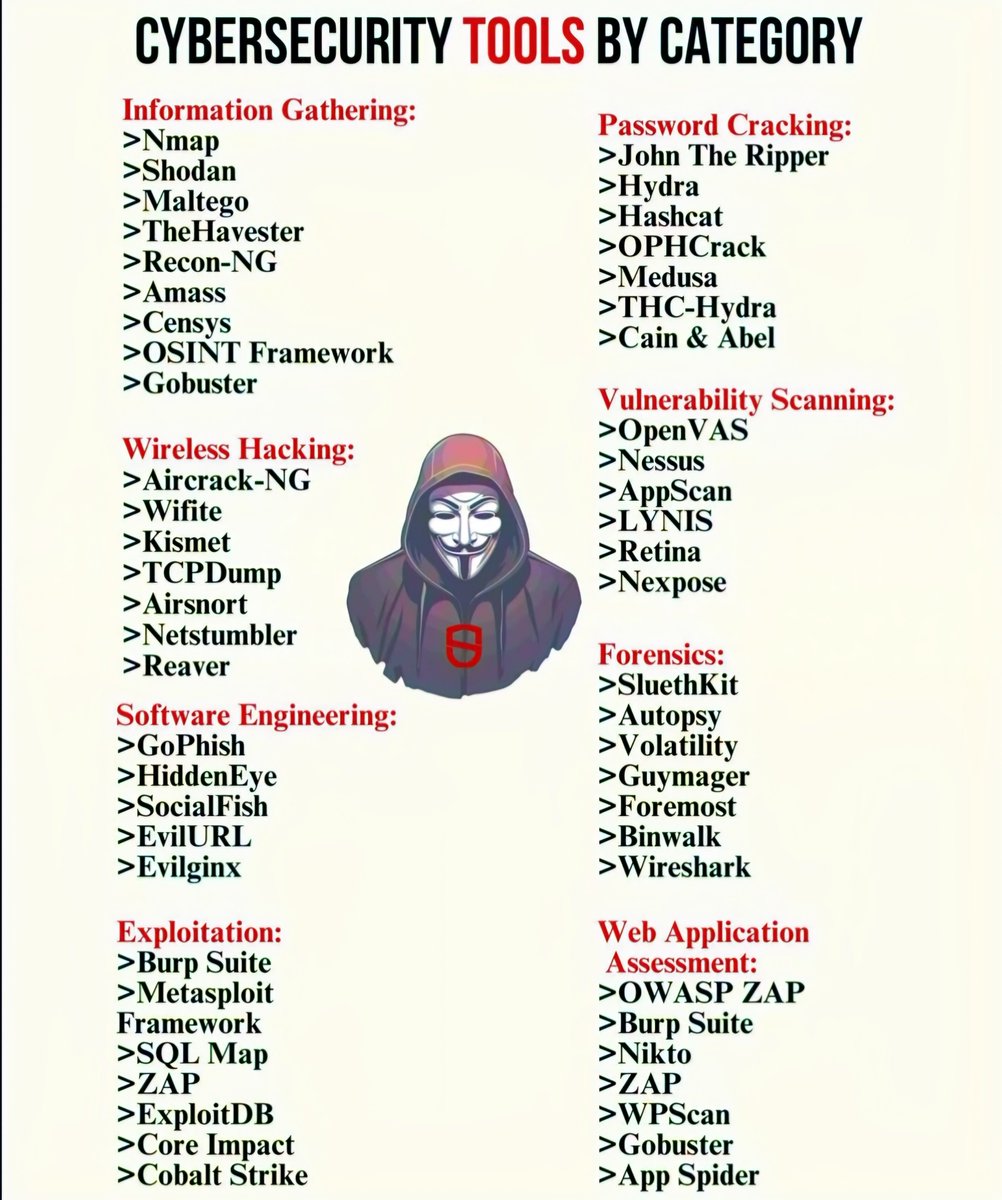
Information Gathering Tools
Information gathering is the first step in any security assessment. These tools help you obtain data about your target system or network, which is crucial for planning further actions.
- Nmap: A powerful network scanning tool that identifies devices on a network, offering insights into open ports and services running on the servers.
- Shodan: Often dubbed as the “search engine for hackers,” Shodan allows users to find specific types of computers connected to the internet using a variety of filters.
- Maltego: A tool that offers visual link analysis, helping security professionals analyze relationships between people, groups, and other entities.
- TheHarvester: Specializes in gathering email accounts and domain information, making it a useful tool for reconnaissance.
- Recon-NG: A full-featured web reconnaissance framework that provides a powerful environment for gathering open-source intelligence.
- Amass: Used for DNS enumeration and network mapping, it’s a complete tool for discovering domain names associated with your target.
- Censys: A search engine that provides a view of the entire internet and is helpful in identifying vulnerable services.
- OSINT Framework: A collection of links and resources related to open-source intelligence, enabling users to gather data more effectively.
- Gobuster: A tool for brute-forcing URIs and directory paths on web servers, helpful in discovering hidden resources.
Wireless Hacking Tools
Wireless networks are often overlooked security points, making them critical for any security analyst.
- Aircrack-NG: A suite of tools used for assessing Wi-Fi network security, focusing on monitoring, attacking, testing, and cracking.
- Wifite: An automated wireless attack tool that utilizes various techniques to crack vulnerabilities in Wi-Fi networks.
- Kismet: A wireless network detector, sniffer, and intrusion detection system that can work with 802.11 wireless LANs.
- TCPDump: A powerful command-line packet analyzer, allowing users to capture and display packet headers.
- Airsnort: A tool for recovering encryption keys by analyzing packets in a wireless network.
- Netstumbler: Simple software for finding open Wi-Fi networks.
- Reaver: A tool used to recover WPA/WPA2 passphrases from routers through brute-forcing the router’s PIN.
Software Engineering Tools
Phishing and social engineering attacks have become prevalent, making these tools essential for testing and securing web applications.
- GoPhish: An open-source phishing framework that makes it easy to simulate phishing attacks against users.
- HiddenEye: A phishing tool that allows users to create fake login pages for various services, collecting credentials.
- SocialFish: A tool designed to create phishing campaigns, allowing users to customize various aspects.
- EvilURL: A tool that allows users to create malicious links easily.
- Evilginx: A reversible phishing tool that bypasses two-factor authentication by intercepting session cookies.
Exploitation Tools
When vulnerabilities are found, exploitation becomes necessary to test the resilience of systems.
- Burp Suite: A popular platform for security testing of web applications, offering tools for scanning and exploitation.
- Metasploit Framework: A penetration testing framework that enables you to find vulnerabilities and execute code against remote target machines.
- SQLMap: An open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities.
- ZAP: An open-source web application security scanner that finds vulnerabilities in web applications.
- ExploitDB: An archive of public exploits, allowing users to look up vulnerabilities and associated exploits.
- Core Impact: A commercial penetration testing tool that allows extensive testing of network vulnerabilities.
- Cobalt Strike: A sophisticated tool for advanced adversaries to emulate and execute penetration tests.
Password Cracking Tools
Understanding password strengths is vital, and these tools can assist in testing password resilience.
- John the Ripper: A fast password cracker supporting multiple encryption algorithms and hash functions.
- Hydra: A parallelized login cracker that supports numerous protocols to attack.
- Hashcat: Known as the world’s fastest password recovery tool, capable of cracking hashes at astonishing speeds.
- OPHCrack: A free open-source tool that uses rainbow tables to recover passwords from Windows machines.
- Medusa: A clean and efficient password brute-forcer that can support a variety of services.
- THC-Hydra: A flexible password cracking tool that supports numerous protocols and is able to perform brute-force attacks.
- Cain & Abel: A password recovery tool for Microsoft Operating Systems, featuring a variety of attacks.
Vulnerability Scanning Tools
Regular scanning for vulnerabilities is crucial to maintaining secure systems.
- OpenVAS: A comprehensive open-source vulnerability scanner that identifies security issues in systems and networks.
- Nessus: One of the most well-known vulnerability assessment tools that discovers vulnerabilities, misconfigurations, and compliance issues.
- AppScan: A solution for detecting vulnerabilities in applications throughout their lifecycle.
- LYNIS: An open-source security auditing tool for Unix-based systems.
- Retina: A vulnerability management tool that delivers in-depth visibility and risk assessment.
- Nexpose: Integrates with various tools for real-time vulnerability management.
Forensics Tools
In the aftermath of a security breach, forensic tools are essential for investigation and recovery.
- SleuthKit: A collection of command-line tools for investigating disk images and recovering data.
- Autopsy: A user-friendly interface that simplifies SleuthKit’s functionality for easier usage.
- Volatility: An open-source framework for memory forensics.
- Guymager: A forensic imager that creates bit-by-bit copies of disks and partitions.
- Foremost: Used for data recovery, particularly file carving.
- Binwalk: A tool for analyzing and extracting embedded files from firmware images.
- Wireshark: A network protocol analyzer that helps in capturing and interactively browsing network traffic.
Web Application Assessment Tools
Web applications can be a target for numerous attacks, making examination tools essential.
- OWASP ZAP: An open-source web application security scanner that helps to find security vulnerabilities automatically.
- Burp Suite: Already mentioned, it not only helps in exploiting vulnerabilities but is also excellent for their assessment.
- Nikto: A web server scanner that tests for dangerous files, outdated server versions, and other common vulnerabilities.
- ZAP: Reiterated here due to its dual role as both an exploit and assessment tool.
- WPScan: A specialized tool for scanning WordPress websites for vulnerabilities.
- Gobuster: Resurfaced for its functionality in discovering hidden resources online.
- AppSpider: Comprehensive tool that automates application security testing.
Understanding and utilizing the right cybersecurity tools can significantly enhance an organization’s security posture. Investing time in familiarizing yourself with these tools can equip you to proactively defend against potential threats in a constantly evolving digital world.