Select Language:
Researchers have uncovered 11 malicious extensions on the Google Chrome Web Store, amassing a staggering 1.7 million downloads. These extensions pose considerable risks to users, including tracking their online activities and potentially redirecting them to dangerous websites.
The discovery was made by Koi Security, a platform focused on security software solutions, which alerted Google to the problem. The story was initially reported by Bleeping Computer.
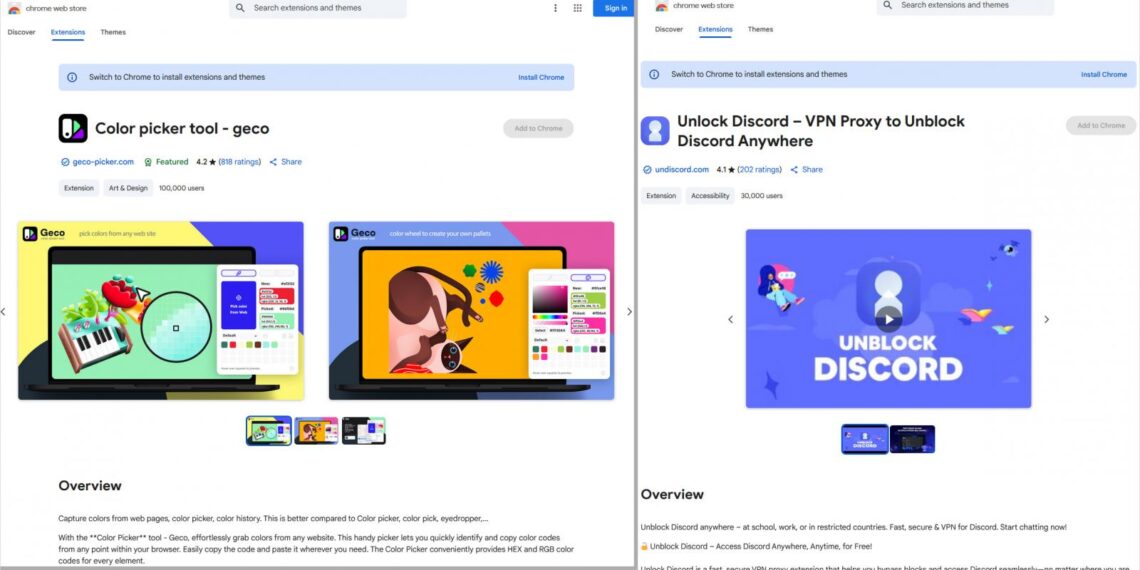
These malicious extensions disguise themselves as helpful tools, such as color pickers, VPNs, volume boosters, and emoji keyboards. They have received positive reviews and have been prominently displayed in the store, creating a façade of legitimacy for unsuspecting users.
Although many of these extensions appeared safe at first, updates later introduced harmful code.
While some of these extensions have been removed from the Web Store, many are still accessible. Users are strongly urged to promptly check for and uninstall the following extensions:
- Color Picker, Eyedropper — Geco colorpick
- Emoji Keyboard Online — Copy & paste your emoji
- Free Weather Forecast
- Video Speed Controller — Video manager
- Unlock Discord — VPN Proxy to Unblock Discord Anywhere
- Dark Theme — Dark Reader for Chrome
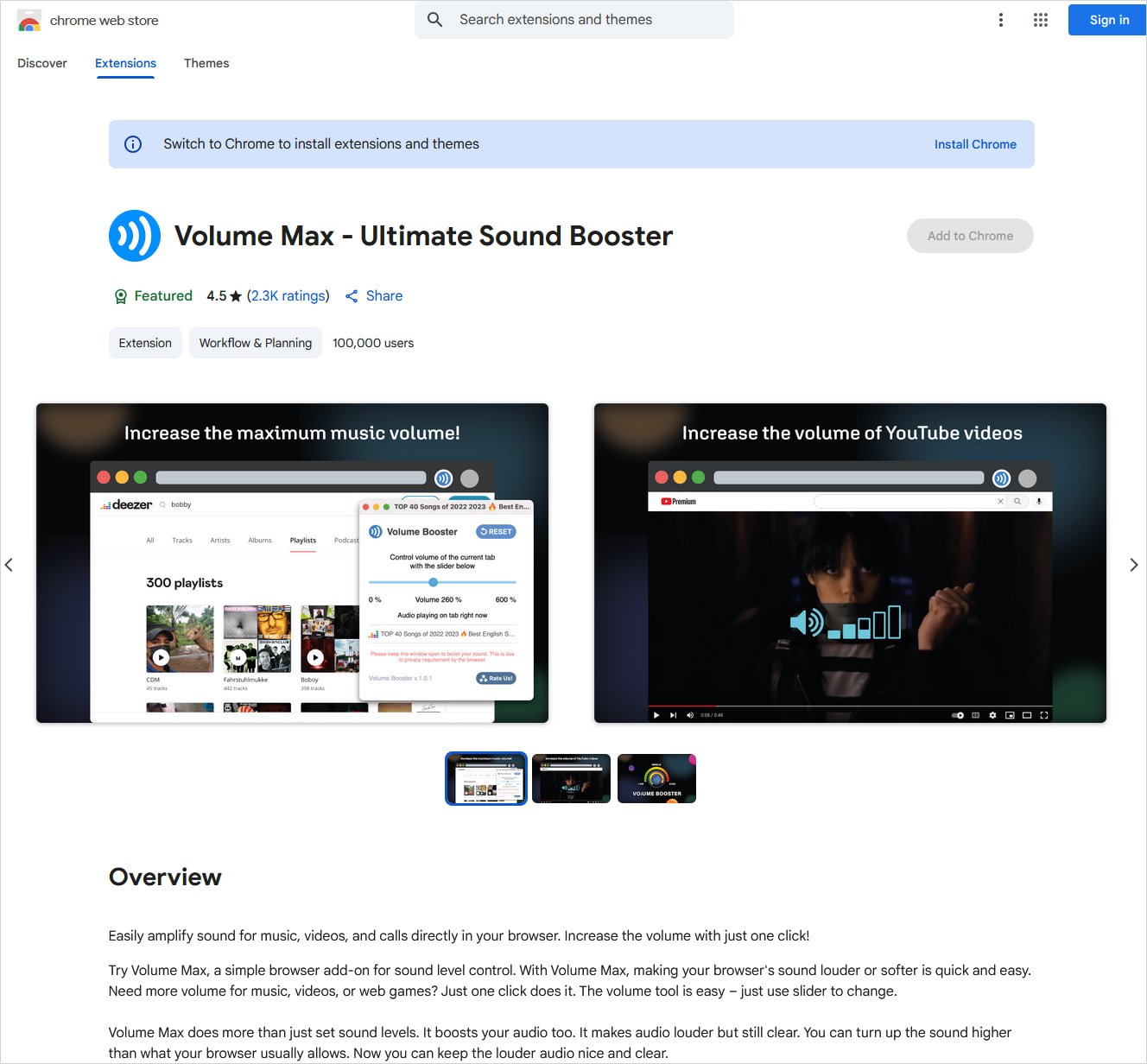
- Volume Max — Ultimate Sound Booster
- Unblock TikTok — Seamless Access with One-Click Proxy
- Unlock YouTube VPN
- Unlock TikTok
- Weather
One notable extension, ‘Volume Max — Ultimate Sound Booster,’ had previously raised suspicions among LayerX researchers, who flagged it for potential spying, although verification of malicious activity was not confirmed at that time.
The main issue lies in the background service worker of each extension, which uses the Chrome Extensions API to monitor users. When users browse new webpages, a listener is activated, capturing the URL and transmitting it to a remote server along with a unique tracking ID.
This remote server can then redirect users to unsafe websites, opening the door to potential cyberattacks. However, Koi Security’s tests have not yet recorded any active redirections.
The harmful code wasn’t included in the initial iterations of these extensions; it was added later through updates.
Google’s auto-update feature quietly installed these updated versions on users’ devices without their knowledge or consent, indicating that the extensions may have been compromised by outside sources over time.
Further investigation shows that similar malicious extensions have also been discovered in the official store for Microsoft Edge, affecting an additional 600,000 users.
In total, these harmful extensions have impacted over 2.3 million users across both browsers, representing one of the largest browser hijacking incidents in recent memory.
Koi Security strongly advises users to remove the identified extensions without delay, clear their browsing data to eliminate tracking identifiers, run a malware scan on their systems, and keep an eye on their accounts for any unusual activity.