Select Language:
With over three decades of experience in the IT sector, my journey has largely unfolded at PC-WELT, Germany’s leading technology publication, where I have focused on cybersecurity. My responsibilities include testing antivirus solutions, providing advice on reinforcing Windows security, scouting for the best security tools, and keeping an eye on criminal activities in the cyber realm.
Throughout my career, I’ve cultivated numerous habits and principles that I regard as essential for safety in the digital landscape. Yet, when I observe the behaviors of everyday computer users, I frequently notice practices that are either risky or lack a security-conscious approach.
This realization has inspired me to compile a list of the top 10 actions that, as a seasoned IT security professional, I would never undertake, along with alternative strategies for safeguarding oneself.
1. Opt for Moving Instead of Copying
Image Credit: IDG
The thought of moving my files instead of copying them is unsettling. This caution particularly applies to unique files like photographs or audio recordings. While losing such files during the moving process is rare, it is a risk I don’t want to take.
Even if the move goes smoothly, the files become available only once. Should the hard drive fail or if I mistakenly delete them, I would lose everything. These hazards are inherent in choosing to move files instead of copying them.
If you find yourself saying, “I need more space on my SD card for new images,” consider investing in a second card. Your data deserves protection. I wait to clear space on my SD card until I’ve verified that my backup plan has successfully saved the copied data on my PC, which I do with a hard drive on a Raspberry Pi network.
Additionally, significant files are automatically encrypted and backed up to the cloud.
2. Save Data Without a Backup
I ensure that all my critical data is automatically backed up. Relying on saved work without a backup is simply too precarious for me. This includes data inputted into apps across platforms, including Android, iOS, or Windows. The absence of a clear backup feature in many apps does not absolve users from being diligent about their data.
A noteworthy incident occurred at two grammar schools in Koblenz, Germany, where a critical error led to the disconnection of several hundred school iPads from the network. Many students had used the Goodnotes app solely on their school-issued iPads, resulting in the complete loss of their written notes during a network failure. The cloud backup, standard for iPads, had been disabled for data privacy reasons, and no other backup solutions were in place. In this case, it was not the students’ fault, but rather the failure lay with the system administrator.
3. Format Storage Without Confirming

Image Credit: IDG
I would never make the mistake of formatting a drive without being certain of selecting the right one; trust me, I have been there. For years, I used multiple external USB drives that had identical folder structures, making it easy to confuse them, especially at late hours when fatigue sets in.
To avoid this mistake, I now clearly name and label my external drives and carefully double-check before formatting. Always verify the drive letter in Windows Explorer before proceeding with any formatting operation.
Related: Strategies to Prevent (or Recover from) a Ransomware Attack
4. Click Links in Emails
Opening links in emails is something I actively avoid, especially those claiming to originate from my bank or payment services. Even genuine messages from PayPal do not prompt me to click links. Why? It’s frighteningly simple for cybercriminals to craft emails that replicate a bank’s communication.
Instead, I visit banking sites and important accounts through bookmarks or by typing in the URL directly. This practice helps ensure that I am accessing legitimate channels. If there’s no message in my customer account, the content of the email is either spam or not significant enough to warrant notification.
Tip: Adjust these 5 Windows settings to enhance your data privacy.
5. Open Suspicious Files

Image Credit: IDG
If I discover a suspicious file, whether it’s software or a document, I’ll avoid opening it. The risks involved are simply too high. As an IT editor, I download numerous tools, most of which get screened by antivirus software. However, files from untrustworthy sources are red flags, whether they are attached to emails or downloaded from ambiguous websites.
When I must interact with such files, I verify them with VirusTotal, an online service that analyzes files against over 60 antivirus engines. For a deeper investigation into suspicious files, I might utilize available online sandboxes, though these can require registration and sometimes incur fees. A straightforward and free option is Hybrid Analysis.
6. Share Vouchers for Service Payments

Image Credit: Foundry
Surprisingly, many individuals fall for such scams. This reflects a broader issue of social engineering, where attackers manipulate emotions like trust and fear to mislead individuals into actions counter to their best interests. A well-planned con artist can ensnare even the most vigilant individuals.
Important: Be skeptical, especially if someone requests payment in the form of gift cards or vouchers.
7. Connect Unknown External Devices
If I encounter a USB drive belonging to someone unknown, I won’t connect it to my computer. While current versions of Windows no longer execute files from USB devices automatically, curiosity can pose serious risks. Malicious actors often label their files enticingly, inviting users to open them.
Historically, it has been noted that to infiltrate a company’s network, all it might take is leaving infected USB drives in accessible locations. Infamous malware like Stuxnet is rumored to have entered critical systems via such methods.
If I absolutely must plug in an unknown USB drive, I adhere to the same verification practices mentioned earlier: using VirusTotal or a reputable sandbox to assess its safety prior to opening any file.
8. Retain Default Passwords
Upon connecting new devices that come with preset passwords, I change those passwords immediately. This same philosophy extends to online accounts that provide me with temporary passwords.
While rare: The practice of routers or devices shipping with default passwords still exists. Attackers exploit these vulnerabilities, thus the need for swift action in securing devices. Utilizing a password manager can significantly strengthen account security.
9. Enable Unnecessary Network Services

Image Credit: IDG
Every month, new vulnerabilities affecting networked devices like NAS or webcams come to light. Thus, I refrain from enabling any unnecessary network services. Examples include turning off remote access for my router, lighting solutions, and smart home devices.
10. Invest in the Priciest Antivirus Version
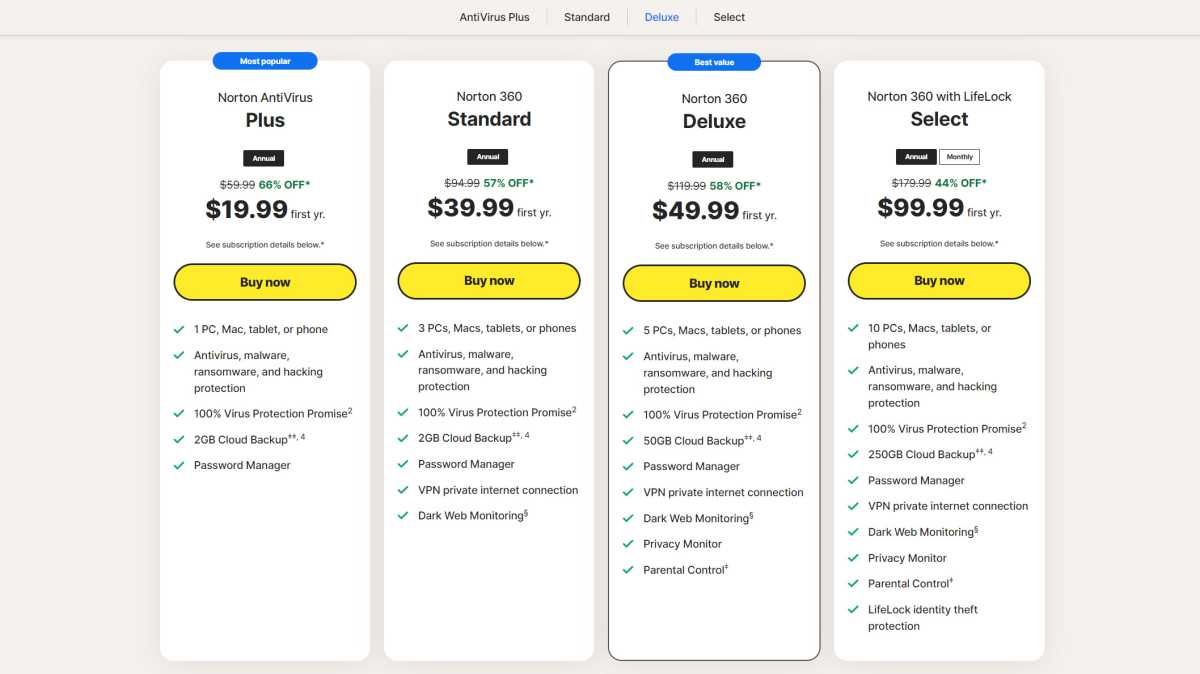
Image Credit: PCWorld
Antivirus software typically offers several versions, from basic to premium. I’ve never found it necessary to purchase the most expensive version, focusing instead on practicality.
My goal is financial prudence: If I had an unlimited budget, I might consider a different option. For now, I select the mid-range version, often labeled as Internet Security. It provides adequate protection beyond what free antivirus tools like Microsoft Defender offer without the excessive cost of premium features I might not need.
Although higher-tier programs provide many appealing extras, I find that I can secure what I need without the added price tag.
This article was originally in German and has been translated to English for broader accessibility.







